Synology NAS Encryption, the Basics
Networking CryptoThis article originally started off as a “Why the hell can’t I enable Mount on Boot!?” query, but after solving that mystery, I decided to dig a little deeper into the operation of Synology NAS encryption. Hopefully this will help you make sense of a somewhat complex issue, especially if you’re not too familiar with encryption in general.
Synology make great products (no, I wasn’t paid to write that). I’ve been using them on and off in my professional career for quite some time, and regardless of whether you’re running a small DiskStation at home, or a beast SA Series in the datacentre, the configuration and management is always simple and easy to use. However, when it comes to the encryption side of things – Synology have left a couple of questions unanswered. I thought I’d write a quick post to clear up some of the common pitfalls when using local encryption for shared folders.
Local folder encryption
Synology supports the ability to encrypt local folders, which is easily achieved by protecting the folder with a passphrase, acting as the key. To unlock the folder, you simply provide the passphrase or the key file. I was unable to determine what type of encryption Synology use for the key file, but either can be accepted when mounting an encrypted volume.
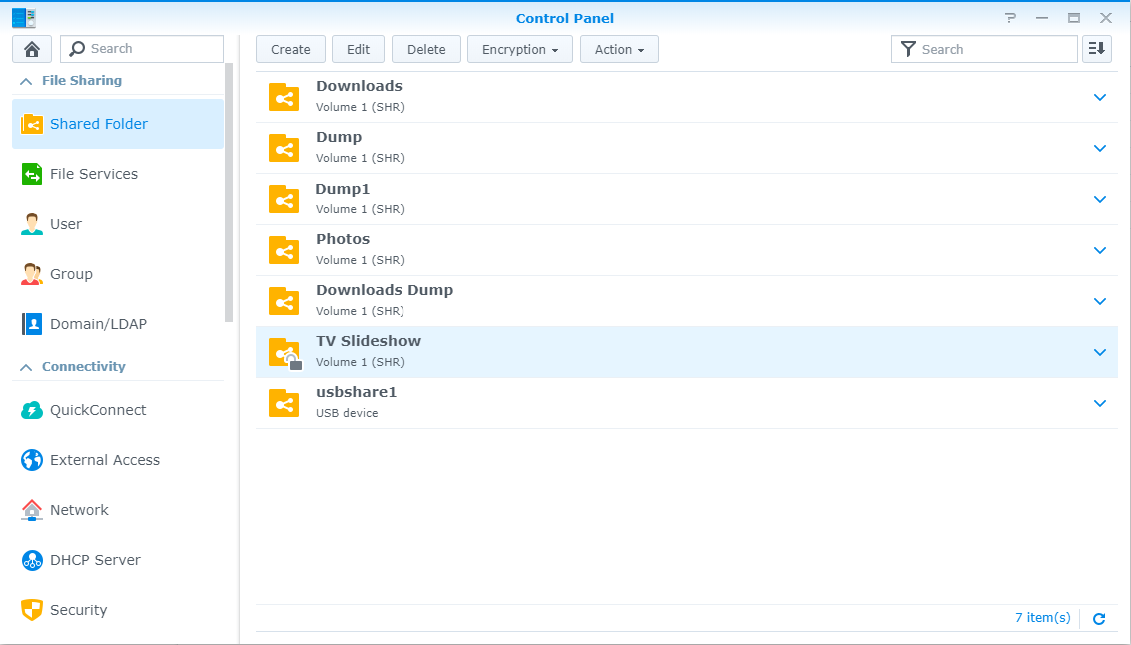
Of course, when the NAS reboots, this encrypted volume cannot be automatically mounted, because the NAS does not know, or store the key\passphrase. We’ll need something on-box to correct that.
Synology Key Manager
To ensure the NAS has access to the keys to decrypt on boot, you can take advantage of the Synology Key Manager. The Key manager needs to live somewhere safe, two options are available:
- System partition on the NAS
- External USB drive
There are a few things to consider when choosing which option you’d prefer. Namely, the system partition forms part of the NAS itself. Meaning if the appliance were stolen\damaged, the keys are lost as well. Storing the keys on the appliance is like storing the house keys under the mat.
So let’s assume we want to follow best practices, and the key will live on an external USB drive. There are other advantages to this. A quick comparison is useful about now:
| System Partition Storage | USB Storage | |
|---|---|---|
| Keys stored away from encrypted data? | No | Yes |
| Cypher used to protect key | Machine ID only | Passphrase or Machine ID |
| Mount on boot possible? | Yes | Only if using Machine ID |
| Passphrase for Key Manager required? | No | Yes |
Obviously the USB option gives us the opportunity to separate keys and data – a good practice in general. But how does the Key Manager protect the keys themselves? It uses a cypher.
A cypher is just a method of encrypting data. Synology uses cyphers to encrypt the keys to your folder, but folders themselves are only protected with a passphrase, like so:
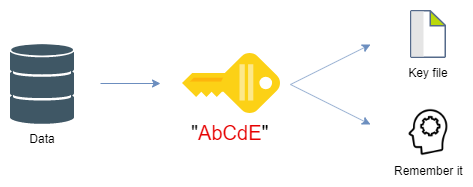
The ‘Data’ folder is now protected with a passphrase. DSM will offer a download once complete, in
our case the file Data.key is created, which contains an encrypted version of our passphrase.
This folder can now be unlocked using the passphrase or the key file, you don’t need to keep both
since the key file is just an encrypted representation of your passphrase. You can choose to save the
key file somewhere safe (i.e. another vault), or write down the passphrase in your password
manager (if you don’t have one of these, you really should be considering it!)
But manually entering the passphrase or uploading the key file on each reboot is tedious. This is where the Key Manager comes in to help.
In short, the Key Manager is a vault for your key files. Because it’s a vault, itself and the keys need protecting too. This is done in a couple of different ways depending on where the Key Manager lives.
Key Manager on System Partition
If you opt the store the Key Manager on the local NAS system partition, there’s no need to configure a passphrase for Key Manager access. I assume this is because authentication already takes place with the wider system and the local encryption of the Key Manager is handled elsewhere. In short, the Key Manager launches, and you can create keys using the Machine ID cypher only.
The big advantage to using the Machine ID however is that you can auto-mount volumes on boot. The setup now looks like this:
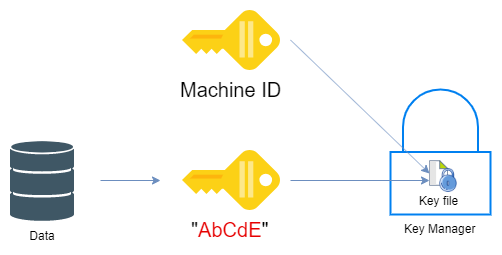
The key file isn’t stored in plain text, it’s encrypted again – using the Machine ID.
Once we configure the individual keys within the Key Manager, we can see that Mount on Boot is available:
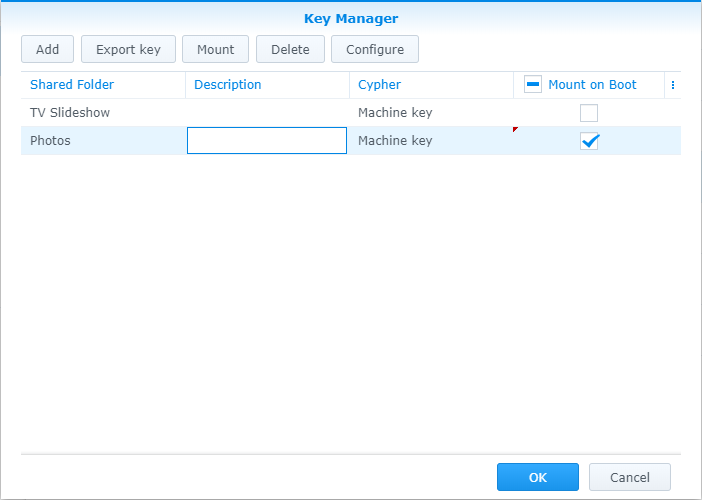
Key Manager on USB
This method is more flexible, but does require additional steps of authentication. Namely the Key Manager will now require its own passphrase, separate from your folders. This is to ensure the Key Manager is protected when not connected to the NAS appliance.
Once you configure your Key Manager to live on a USB drive, you gain an additional option to protect the keys within the vault – passphrase. This option has one major drawback, it will not support Mount on Boot. One advantage however is you no longer need to remember the keys to the individual folder, as you can simple mount volumes using the master passphrase for the Key Manager (I’ll admit, this sounds like a terrible idea though. If the USB stick is destroyed, you’ll have no means of obtaining the keys from the Key Manager. A local backup of your drive or the individual folder keys is wise).
Full documentation for the encryption features can be found here:
https://www.synology.com/en-us/knowledgebase/DSM/help/DSM/AdminCenter/file_share_key_manager
